Cloudflare is one of the most well-known DNS services. Apart from its CDN features, it helps websites owners to protect and firewall their website. Their reverse proxy service is considered a good way to anonymize a website and its hosting server IP details. This way the origin IP address is hard to find and used in DDoS and other malicious attempts to bring down or hack a website and the network supporting it.
In the following guide, we’re going to show you 3 ways you can test your website and see if Cloudflare is actually protecting its real IP address out of the public eye. The following tests are also used by us when doing a security audit in our client WordPress websites.
1. Ask the Target Website to email you back
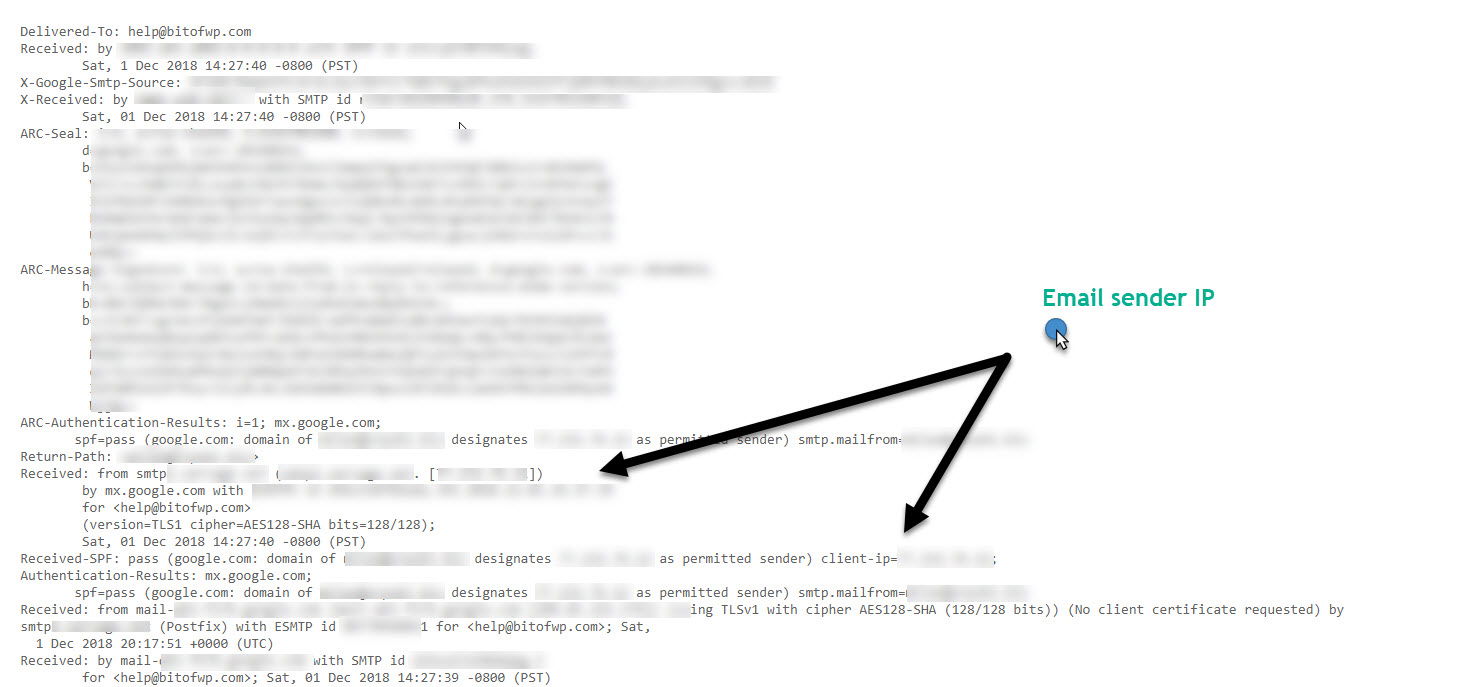
One of the easiest ways to resolve the real IP address for a website behind the Cloudflare Proxy is to force it to send an email back to you.
This can be achieved by registering an account or using the “forgot password” feature or sending a real question or comment through the target site contact form. Once you receive an email reply view its source code and search for the sender’s client-IP. If there is no 3rd party acting as the email service or another dedicated server acting as the mail server then its possible to grab the IP you’re looking for.
2. Check target site domain DNS Records, locate its historical DNS records
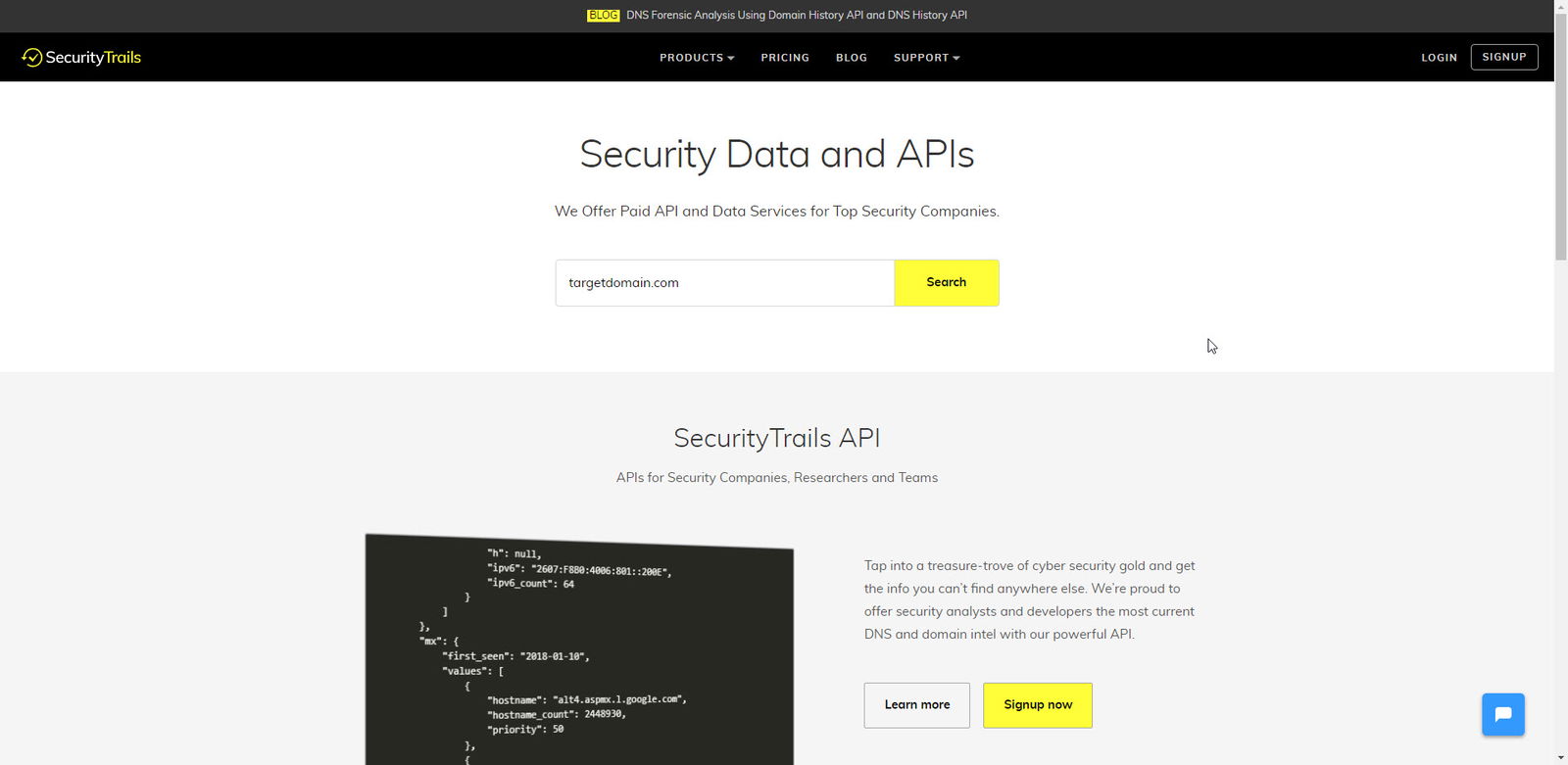
1. The first step is to visit SecurityTrails and run a query for the target domain.
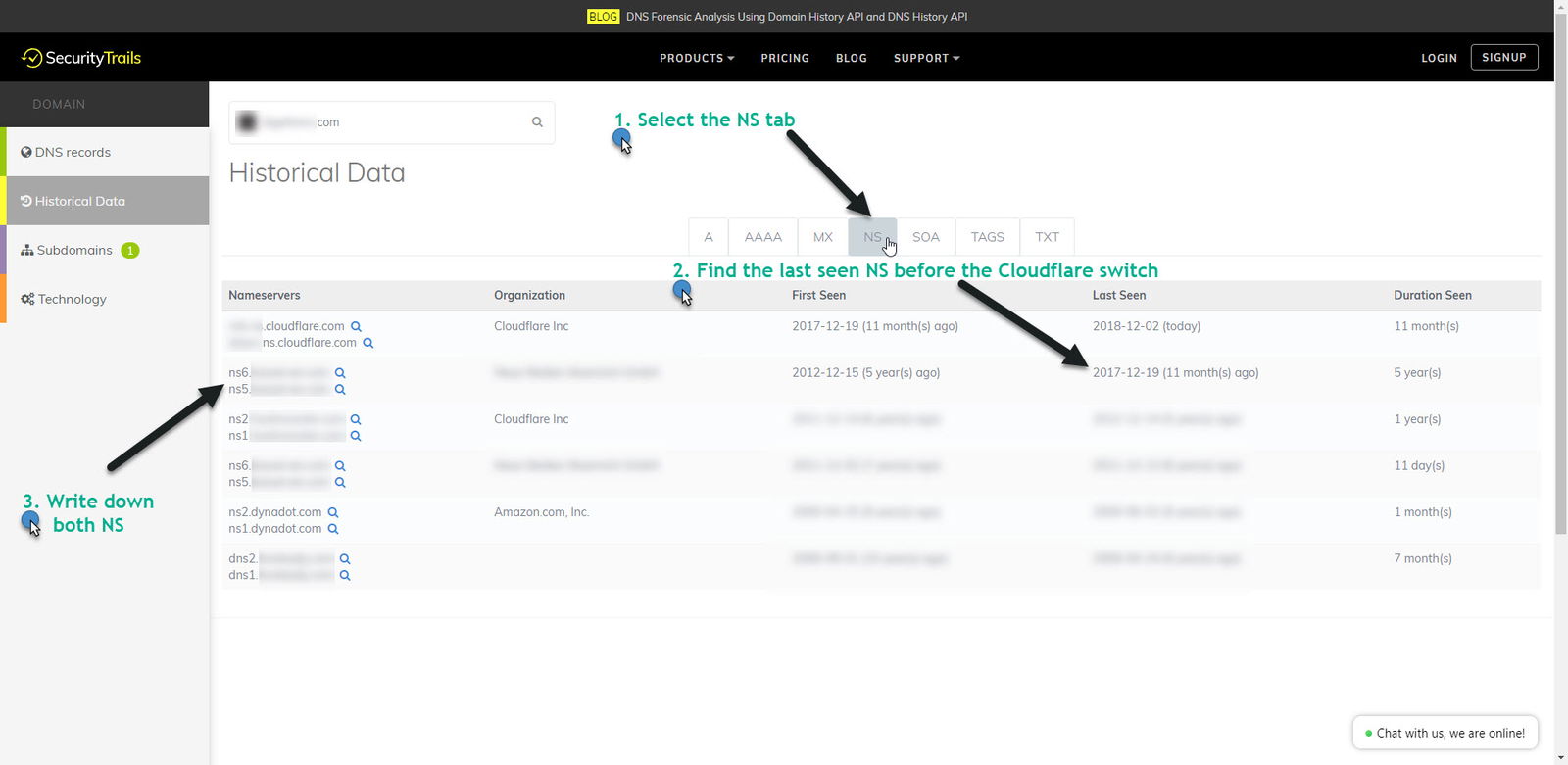
2. Then visit the NS tab and search for the first real NS results before the target domain started using Cloudlfare NS and write them down. You will need those for the next step of this short guide on how to reveal a website real IP hidden under behind Cloudflare’s service.
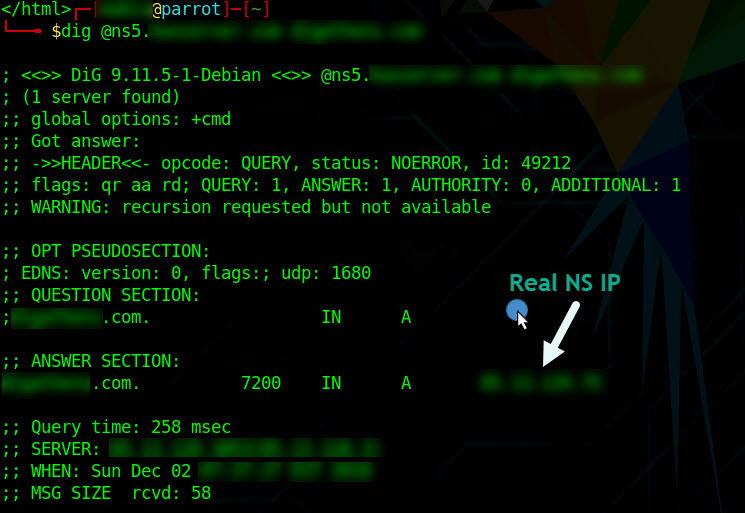
3. For this step, you will need to use a Linux box or set-up a Linux VM using VMWare, run an ssh client and execute(!) the following dig DNS lookup command. Replace targetnameservers.com and targetdomain.com with the nameservers found in the previous step and your own target domain:
dig @ns1.targetnameservers.com targetdomain.com
repeat for all ns records and write down the A IP record(s).
4. This is the last step and it will help you identify that the IP you grabbed from the previous step is actually the one that your target site is sitting on. We’re going to using the ssh client once more and run the following command in order to fetch the HTTP content for your target site.
Make sure to replace the targetdomain.com with your own target domain and the 100.100.100.100 IP with the A IP record(s) found in the previous step.
curl -H “Host: targetdomain.com” 100.100.100.100
If the target site is using HTTPS then add the -k switch to the curl command:
curl -H “Host: targetdomain.com” -k https://100.100.100.100
If the curl result is the same same as the HTML source of the target site homepage then you’ve just found its real IP address!
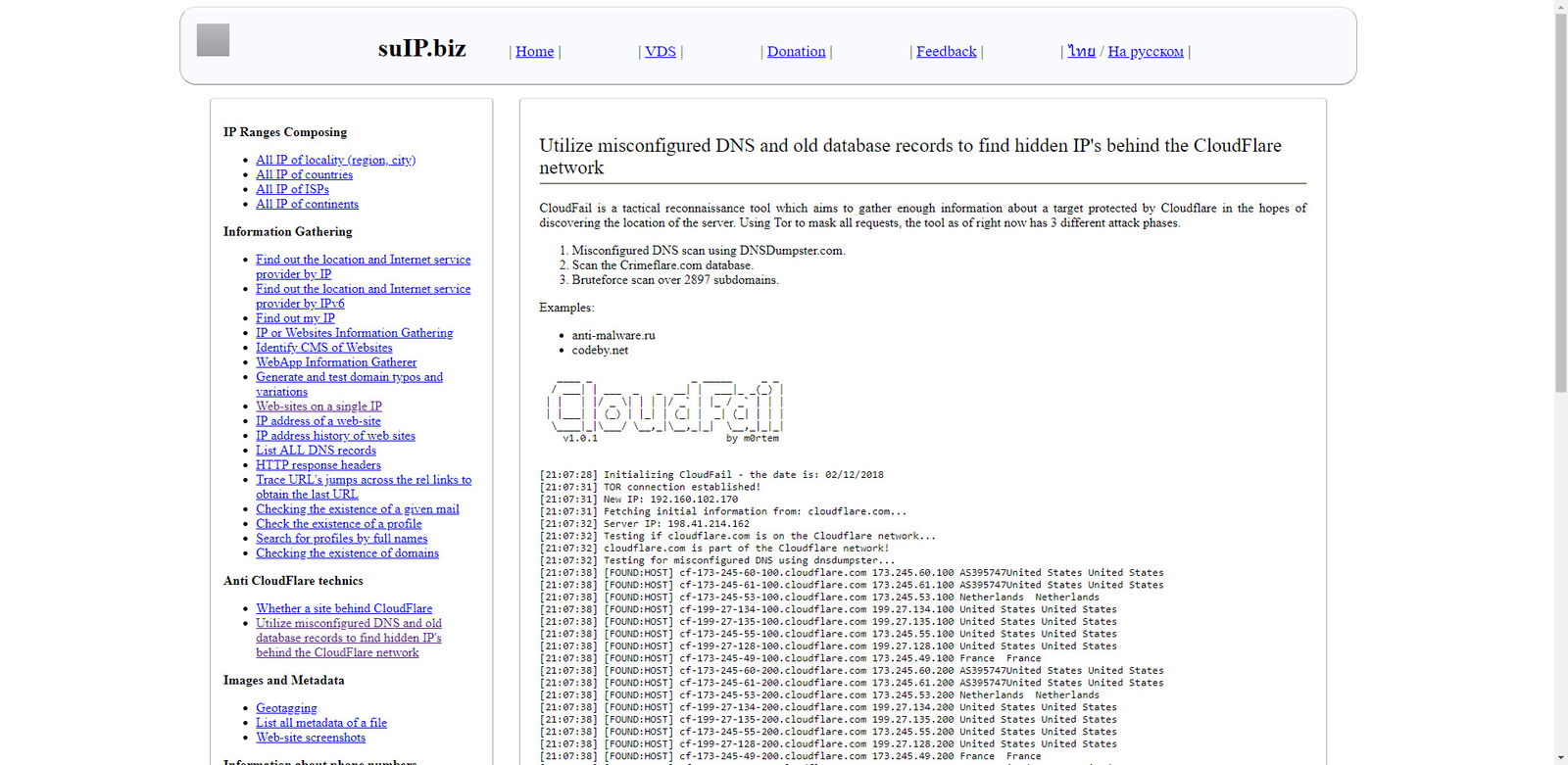
3. Use Cloudfail through an online service
This is the easiest and laziest way to retrieve an IP for a site behind Cloudflare’s Proxy. It’s also the less effective so I suggest to use them with caution. This online service is actually utilizing a Python script called Cloudflare and can be installed in your Linux or Mac box.
Conclusion
My favourite method of retrieving the IP for a WordPress website using Cloudflare is by far the 2nd one where I analyze the website’s domain NS history. This way I get a better idea of the website domain and hosting history along with any vulnerabilities which may be waiting to be exploited.
You can use all three of the methods and see which one works best for you or can subscribe to our WordPress Maintenance Services and let us audit, secure and support your WordPress site.
Disclaimer
This guide is about testing and securing your own websites. If you decide to use it against a website you don’t own then make sure you have an action by written consent from the website owners.
We also have a free API and open for this using our scanning servers and logging domains daily making them publicly searchable.
https://cloudsearch.cf/
Hello Lewis! Are you interested in creating a guest post showing how can someone use your service in order to track down a domain owner? Also apart from the API do you offer an end user solutions like domain scanning?