UPDATED: 14th July 2020
Let’s start this tutorial with a tip, if you want to know your site has been infected by the monit.php hack add your site URL before this snippet and browse it:
/wp-admin/options-general.php?page=monit
If you see a page opening with settings and text strings then you’re most probably hacked, if not you’re probably safe. In both cases I suggest to follow the cleanup guide for the ofgogoatan.com redirect hack.
Monit.php flagged as malware
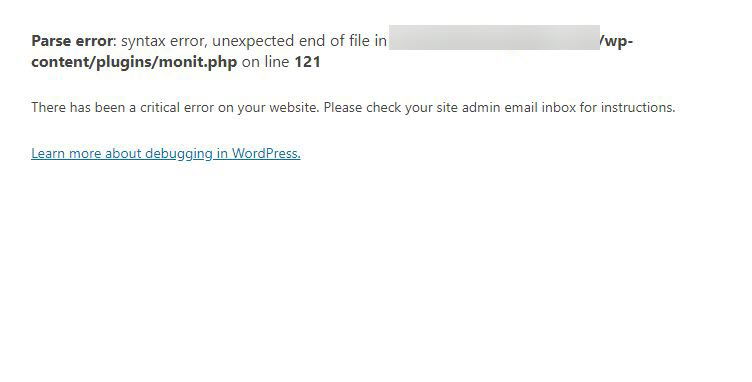
A few days ago we have been contacted by a client who was looking to clean his site from malware.
While working on his site he noticed that some random code was injected to his backend. After scanning his site using WordPress security plugins he found out that more than one files were infected by the monit.php malware.
Monit.php Malware Code Inspection
While fixing this hacked WordPress site we noticed pretty quickly that there was a weirdly named plugin called Monitization in its plugins page. When we inspected the plugin’s code we found out that it was injecting our client’s WordPress site wp_options MySQL table with spam URLs and redirects along with some other settings. Even though the code of this malware is lame overall it can be used as an example of how hackers try to take advantage of infected WP sites for promoting their Black Hat SEO campaigns.
Actually it seems that the monit.php hack is trending on WordPress security forums, you can find a lot of WP users posting topics related to it like this one here or here or here saying that their WordPress site is redirected to ofgogoatan.com.
How to Remove the Monit.php Hack
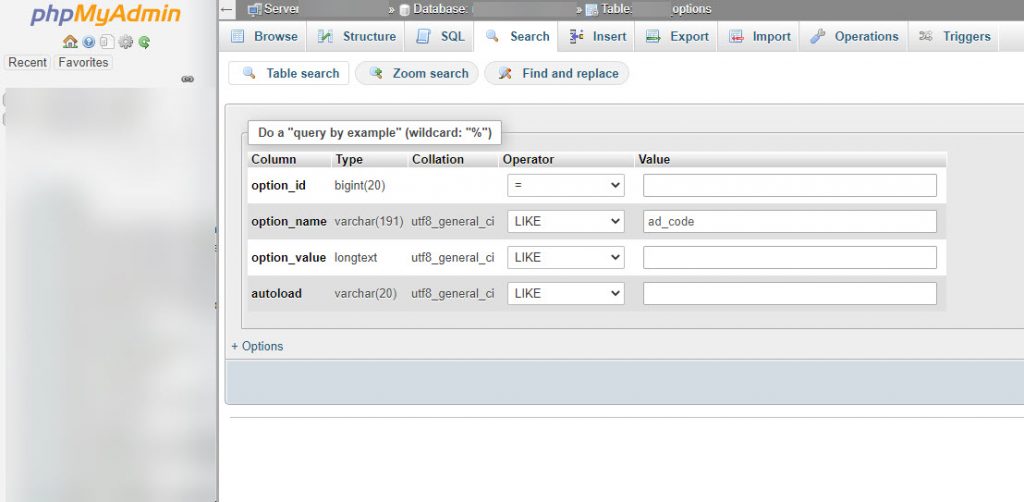
Apart from cleaning all of your WordPress site files from the malware redirect hack and deleting the monit.php file under the plugins directory, you will also need to access your database using phpMyAdmin, then browse to your wp_options database table and search for the following option_name records:
- default_mont_options
- ad_code
- hide_admin
- hide_logged_in
- display_ad
- search_engines
- auto_update
- ip_admin
- cookies_admin
- logged_admin
- log_install
Finally, if you find any of those records present delete them but first make sure you have created a backup for your WordPress site first(both the site files and its MySQL Database).
Umar created the following MySQL select statement which you can use on your phpMyAdmin and find if there are any records injected by the Monit malware.
SELECT * FROM 'wp_options' WHERE option_name IN ( 'default_mont_options','ad_code','hide_admin','hide_logged_in','display_ad','search_engines','auto_update','ip_admin','cookies_admin','logged_admin','log_install')The last step is to remove the admins_ip.txt file found in the plugins directory as well.
Looking for Malware Cleanup Services?
We offer critical support to all hacked WordPress site. If your own WordPress installation has been infected by the Monit hack or any other hack then you can submit a malware removal request and we’ll get back to your right away.
Hey Thank you for this and for the links to the topics!
This is very helpful. I am cleaning one of my client’s site with this.
Please add this query into your post somewhere, It will help many people out there.
SELECT * FROM `wp_options` WHERE option_name IN ( ‘default_mont_options’,’ad_code’,’hide_admin’,’hide_logged_in’,’display_ad’,’search_engines’,’auto_update’,’ip_admin’,’cookies_admin’,’logged_admin’,’log_install’)
Thanks a lot, Umar!
Thanks team, helped removed the hack from one of our website. We cleaned the files from plugin page but needed help cleaning up those database files.
Thanks heaps
That’s great news Stephanie!
Thanks a lot for this guide. I was bit lost after going through many articles without proper success. Thanks to you I could simply get rid of this annoying malware.
And many thanks to Umar as well for the nice query.
Thanks, a lot!
I got error:
SELECT * FROM ‘wp_options’ WHERE option_name IN ( ‘default_mont_options’,’ad_code’,’hide_admin’,’hide_logged_in’,’display_ad’,’search_engines’,’auto_update’,’ip_admin’,’cookies_admin’,’logged_admin’,’log_install’);
LIMIT 0, 25
#1064 – You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ”wp_options’ WHERE option_name IN ( ‘default_mont_options’,’ad_code’,’hide_admin’ at line 1
Thank, It’s working.
After adding database name.. it’s working
SELECT * FROM `DATABASENAME`.`wp_options`
Good morning hello I was a victim of this Monit.php marked as malware, friends I have a problem on my website created with wordpress and woocommerce, recently after installing some add-ons I created this monit.php and following this manual to eliminate it I Some new files that were created attract a lot of attention, these files are in many folders and sub folders, they are Index.php files and inside all these files have the same code, here is the link https://mega.nz/file / M5hDgAjY # fAsmuW3blah3zctdbMA1Ige_lP694jmzCCjxSo0xBLU
to see if you can tell me what the function of these files is and why they were created. I will be grateful for the definition of reading this file. Thank you thank you thank you…
Hey there! Did you try following our guide for removing the Monit malware?
Mysql Query should be:
select * from `wp_options` where (`option_name` like “%default_mont_options%” and `option_name` like “%ad_code %” and `option_name` like “%hide_admin%” and `option_name` like “%hide_logged_in%” and `option_name` like “%display_ad%” and `option_name` like “%search_engines%” and `option_name` like “%auto_update%” and `option_name` like “%ip_admin%” and `option_name` like “%cookies_admin%” and `option_name` like “%logged_admin%”)
Thanks, very helpful!!
LOVE U GUYS!
THANK U SO MUCH!!!!
THIS WAS ON OUR WEBSITE FOR PAST 4 MONTHS! CUDNT FIND THE ISSUE
The query Umar created — the single quotes around wp-options should be back ticks ( ` ) , found below the escape key
Make sure to replace the wp_options with the name of your options table in your database as it may be different, but it will contain the word “options: in it. Also, replace the ‘wp_options ‘ single quotes surrounding it with backticks instead, only for the ‘wp_options ‘ part. That should work.
Make sure to replace the wp_options with the name of your options table in your database as it may be different, but it will contain the word “options: in it. Also, replace the ‘wp_options ‘ single quotes surrounding it with backticks instead, only for the ‘wp_options ‘ part. That should work.
Example of what worked for me:
SELECT
*
FROM
`custombnamecoptions`
WHERE
option_name IN(
‘default_mont_options’,
‘ad_code’,
‘hide_admin’,
‘hide_logged_in’,
‘display_ad’,
‘search_engines’,
‘auto_update’,
‘ip_admin’,
‘cookies_admin’,
‘logged_admin’,
‘log_install’
)