Malicious JavaScript code can be injected into Popups
Several security flaws have been uncovered in the Popup Builder plugin code. Currently, this plugin has more than 200,000 active installs. Many site owners are still unaware of the issue. This plugin is regularly updated and maintained by the authors. However, it took them 7 days to release the patched version of the plugin. Meanwhile, many sites were exploited by hackers and those using an outdated version of the plugin are still at risk.
One of the vulnerabilities tracked as CVE-2020-10196, can be used to collect the list of subscribers. Apart from that, an attacker can gather system configuration info and grant access to certain features of the plugin. This does not grant admin privileges to the attacker.
However, the second vulnerability tracked as CVE-2020-10195, allows hackers to insert malicious JavaScript inside the popup. The JavaScript would then be executed every time the popup loads. The intention is to redirect users to a phishing site, online pharmacy or other sites that cannot be legally advertised. However, if the popup is displayed to a logged-in user (such as admin), the malicious JavaScript can be used to get his credentials. The attacker would then be able to log in as an admin. They would also be able to create other users with admin privileges.
If you were using any of the outdated versions of the Popup Builder plugin, keep reading. You will find useful information below regarding the vulnerabilities and how to check if your site has been compromised.
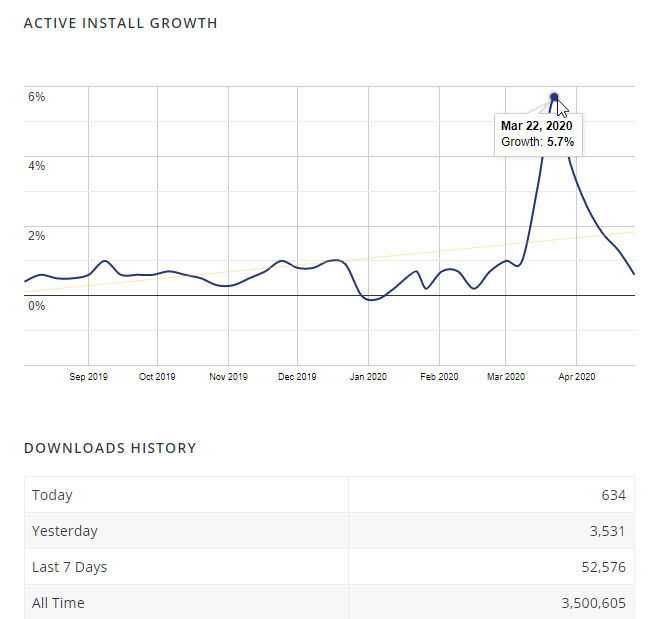
Notice: It’s interesting to see that one month after the vulnerability was published the plugin has doubled its Active Installations from 100,000 to 200,000.
Who are the attackers?
The attackers will remain nameless and faceless for now. However, those researching the vulnerability have identified several domain names that were used in the attacks.
Some researches have reported that malicious JavaScript redirect visitors from hacked sites to following URLs:
- collectfasttracks[.]com
- lightversionhotel[.]com
- winworker[.]club
- verybeatifulantony[.]com
The first listed domain has many subdomains that were also used for malicious redirects such as:
- dest.collectfasttracks[.]com
- best.collectfasttracks[.]com
- step.collectfasttracks[.]com
- clon.collectfasttracks[.]com
One of the IP addresses that was often associated with the attacks is 45.9.148.79.
When was the hack first reported?
Defiant, the company that created the WordFence plugin, was the one that discovered the plugin vulnerability. They have privately informed the authors of the Popup Builder plugin on March 4, 2020. After that, the plugin authors have sent them a patched version on March 6, 2020. Defiant reviewed it and suggested how to strengthen the security further.
Five days later, on March 11, 2020, plugin authors released the fully patched version 3.6.41 of the Popup Builder plugin.
How to check if your site has been compromised?
Have your visitors/subscribers reached out to you and complain about malicious activity?
If you were using an outdated version of the plugin, there’s a chance that someone has already exploited the plugin vulnerability. One of the first signs of trouble is redirects. If your visitors have complained about the site redirecting them to suspicious URLs, this is a big red flag. If attackers collected the subscriber list from your site, they might try to send emails to your subscribers. They would make it look like the emails are coming from you. However, the messages would contain malware in the form of links or downloadable files.
Are there any new admin users that you don’t remember adding?
This is a major concern. Someone with admin privileges can do anything with your site. They can change appearance, add content as they please, add or delete users. Though unlikely, they can even deface the site or delete it entirely.
Inability to access wp-admin dashboard
This does not necessarily mean that someone hacked your site. Plugin conflicts, update failures, and corrupt plugins can cause this. However, if you can’t access the wp-admin dashboard and it redirects you to another site in the process, then you can be absolutely sure there’s malware on site. Especially if your site redirects you to one of the domains mentioned earlier in the article.
Also, if you notice any changes in admin email, WordPress settings or similar, that should confirm your suspicions.
How does the hack work?
The plugin allows malicious users to add custom JavaScript to popups which runs every time those popups load. The plugin also has the functionality to automatically save unpublished drafts. To do this, plugin authors registered a WordPress hook inside the Popup Builder. Hooks allow one piece of code to communicate with the other. In this case, it allows the plugin to communicate with the WordPress core.
However, this hook was available to unauthenticated attackers. Furthermore, the function it called contained vulnerable code. It allowed attackers to access popups and change their Custom JavaScript and add malicious code. This is called ‘Unauthenticated Stored Cross-Site Scripting’ or XSS.
In addition to that, a few other hooks were faulty. These hooks allowed the attacker to download the subscriber list in CSV format. They could also add admin privileges to any user (over the plugin only) and get sensitive system information. By getting information, an attacker could get a list of plugins and exploit any other outdated and vulnerable plugin.
How can this hack be removed?
1. Update Popup Builder plugin
The first obvious step is updating the Popup Builder plugin. The latest version is 3.65.1 and it is available at the WordPress plugin repository. You should also check all of your popups (including drafts) for malicious code. Remove any JavaScript from the Custom JavaScript section that you don’t recognize. You might need the assistance from a developer or a professional malware removal service. If you don’t have basic JavaScript knowledge, you will not be able to recognize malicious code.
2. Scan your site
You can ask your hosting provider to scan your site or use a malware scanner like Maldet. It will show you if the WordPress core and plugins have been compromised. It is a wise idea to download the latest versions of the plugins you use and replace the files on the server.
Replacing the theme files might not always be possible since this will erase any hardcoded customization. You can look for malware code in header.php, functions.php, footer.php files in the theme directory. Again, using a professional service is the best way if you don’t have at least basic coding knowledge.
3. Remove any suspicious users
Log in to the wp-admin dashboard, then go to ‘Users’. Check admin users and remove any that you don’t recognize. Sorting through subscribers will not be that easy. If you have thousands (or tens and hundreds of thousands) of subscribers, it would not be possible. It’s ineffective to just browse through the list and remove those that look suspicious. First of all, you will not be able to tell with certainty which of the subscribers might be concealed attackers.
One of the safest things to do is reset user permissions and capabilities. You can use the ‘PublishPress Capabilities‘ plugin. If any subscriber has admin permissions, this will revert them to default. If you are using any membership plugin, this can break the plugin setup. Check if that membership plugin has an option to reset permissions to its default values.
It should go without saying that you should reset your admin account password. If there’s more than one admin on the site, everyone should reset their passwords.
4. What to do if the wp-admin dashboard is inaccessible?
If your WordPress dashboard is inaccessible or redirects you to another site, it means that the attacker has tampered with the database. There are two specific values in the database, ‘siteurl’ and ‘home’. The ‘siteurl’ stores the main URL of the site, while ‘home’ points to the home page. Adding a code to wp-config.php can change them.
You should look for a code like this:
define( ‘WP_HOME’, ‘https://example.com’ );
define( ‘WP_SITEURL’, ‘https://example.com’ );
If these lines are not pointing to the URL of your site, remove them.
You can check the database by accessing it via phpMyAdmin. You should look for the ‘options’ table (wp_options) and find ‘siteurl’ and ‘home’ rows. It is possible that the URLs in those rows won’t match your site URL.
All of this requires access to the hosting server either via FTP, cPanel or any other interface your hosting provider offers.
Restoring a backup
Restoring a working backup of your site will save you all the trouble. You won’t have to go through any of the steps described in the previous chapter. However, there are a few things to consider.
First – you can’t know for sure if the backup you are restoring is malware-free. It is possible that the site was already compromised when the backup was made. Unless you are restoring a backup made a while ago.
Second – if you are restoring an older backup, you might lose some content. Posts and pages that you added in the meantime. An additional problem is if you are running an e-commerce or a membership site. This will delete all of the user accounts created between now and the date of the backup.
Third – restoring an old backup will restore old plugin versions. Clearly, plugins that are out of date are a major security risk and that is the opposite of what you want to achieve.
Looking for help in removing the WordPress Popup Builder Hack?
It is understandable that this can be overwhelming for an average user. It is important not to panic but react quickly.
If this sounds too complicated for you, check our WordPress Hacked Fix Service and we will scan, clean and secure your WordPress the site for you in24 hours or less.
Leave a Reply