The WooCommerce Checkout Manager has been reported by PluginVulnerabilities.com for being vulnerable in arbitrary file uploads. The exploit could be activated by an unauthenticated remote attacker when the plugin “Categorize Uploaded Files” option is enabled.
In this case, the attacker cloud brute-force or guess an existing order id number and execute arbitrary server-side script code in the WooCommerce website with the active WooCommerce Checkout Manager plugin.
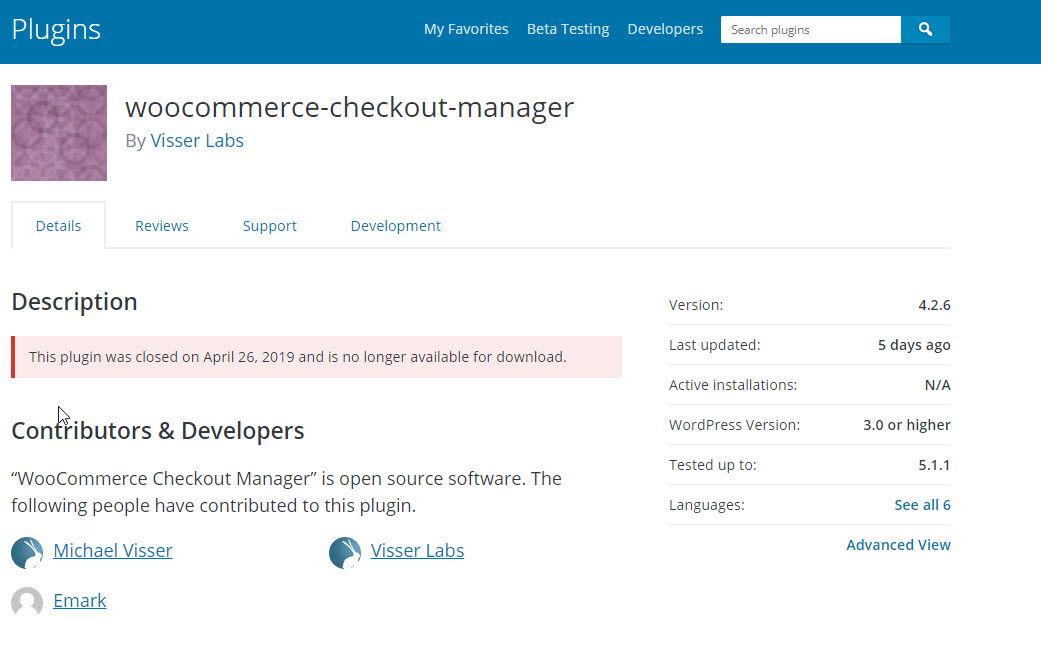
Apparently, WooCommerce Checkout Manager vulnerability was caught by the WordPress repository review stuff which resulted in de-activating plugin’s listing for wordpress.org.
If your WooCommerce website is using the WooCommerce Checkout Manager plugin then you should either disable “Categorize Uploaded Files” option in the setting or disable and remove the plugin completely until a new patched version becomes available from the plugin developer.
Leave a Reply