WP GDPR Compliance Vulnerability
Updated: 18 November 2018
If you recently discovered that your WordPress site had one or two new admins added under the names of t2trollherten and t3trollherten then your site is probably hacked already!
The Story
Once upon a -recent- time, there was a new set of privacy regulations published by the European Union to replace the Data Protection Directive which was first published in 1995. These rules are called General Data Protection Regulation(GDPR) and are recognised as law across the EU. The law also applied to all sites which had EU citizens as visitors, this included WordPress sites as well.
Having a WP site GDPR compliant was(and still is) a hard task. For this reason, many developers thought of creating WordPress plugin to satisfy this need and make life easier for both WordPress site webmasters and users. One of those plugins is WP GDPR Compliance currently actively used in more than 1000,000 WordPress sites.
The bad news is that WP GDPR Compliance in its latest version, up to 1.4.2(now patched), had a serious vulnerability which let unauthorized admin access to WordPress sites Dashboard.
How
The type of vulnerability found in WP GDPR Compliance plugin is falling into the “Privilege Escalation Flaw” category because it allows anyone who can access the site to exploit the plugin and add an admin user giving them the right to add/remove/edit your site file and database contents. This way hackers will have complete control of your site and spread malware to your visitors through Drive-by attacks and zombie attacks to other sites or online services.
Detect
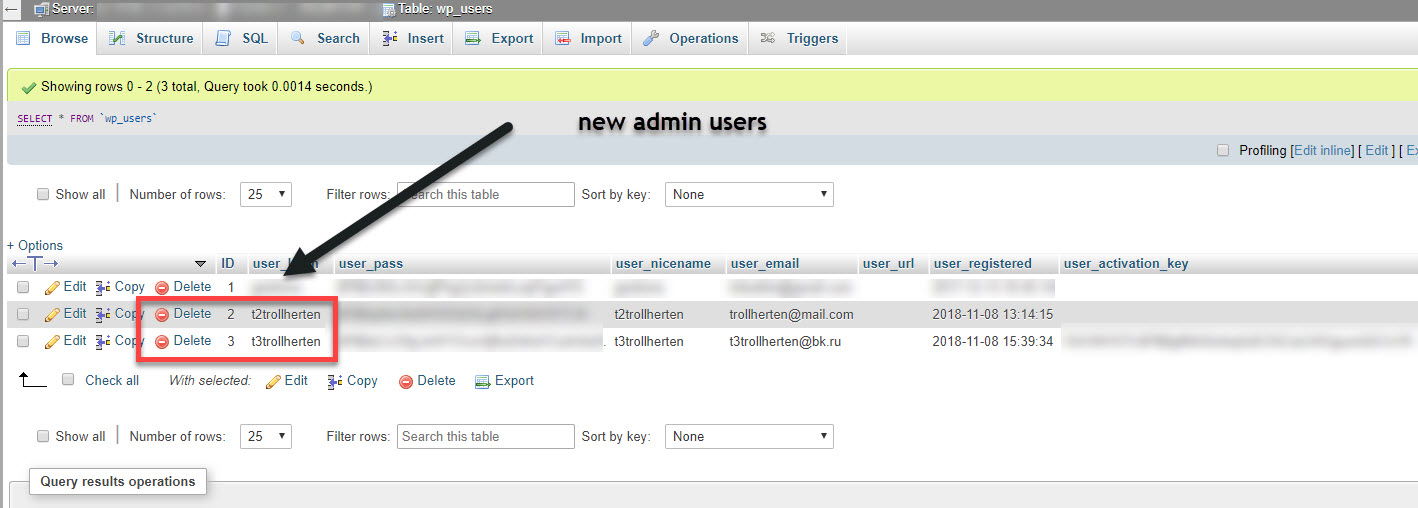
You can find indicators of being compromised by visiting your admin user page and search for any non-authorized admin usernames especially ones under the names of t2trollherten or t3trollherten.
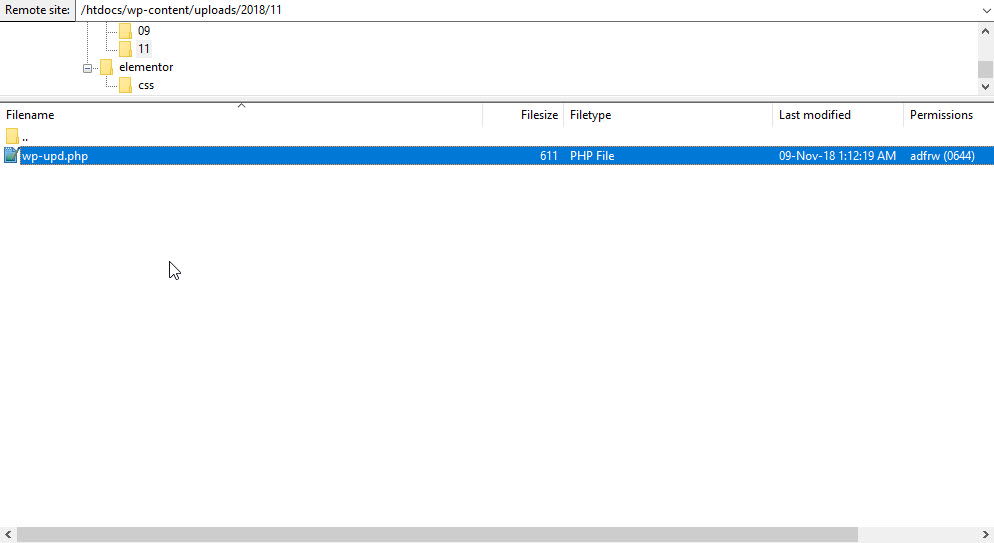
You should also check any file under the name of wp-cache.php found in your WP /wp-content/plugins directory or wp-upd.php under your wp-content/uploads directory, especially if its creation or modification date is recent.
What to do
The first thing to do is to remove the unauthorized admins and de-activate and remove WP GDPR Compliance from your site. Then you should do a clean install from WordPress.org repository and start inspecting your WordPress site for any other signs of exploitation. You can also restore a clean site back up and run re-install the WP GDPR Compliance plugin.
If you feel that you need help in cleaning malware from your WordPress site or you’re keep getting hacked even though you already removed the malware then you need to consult a professional WordPress malware removal service.
Leave a Reply