A few days ago, we received a hack removal request for a WordPress website using both Malcare and WordFence; it kept getting hacked and injected with Japanese spam malware repeatedly.
The site owner told us that he found two scripts injected into his WordPress site; the first one was located under the site’s root directory with the name sw.js, while the other was sitting under wp-includes/js directory with the name font.js. The owner also mentioned that they suspect there is a backdoor which is used to keep infecting their site again and again.
While auditing the site for malware, we immediately confirmed the site owner’s findings; we also noticed that the date of modification for both files was the same, November 11th 2022, so we used this date for running a Linux search which reported all files created or modified under the same date.
Luckily our client was using Cloudways as his hosting service, so we had all the tools we needed to audit and clean up his hacked WordPress site available. In this case, we used Cloudway’s build in SSH client to run the following command for fetching all files created or modified under that specific date.
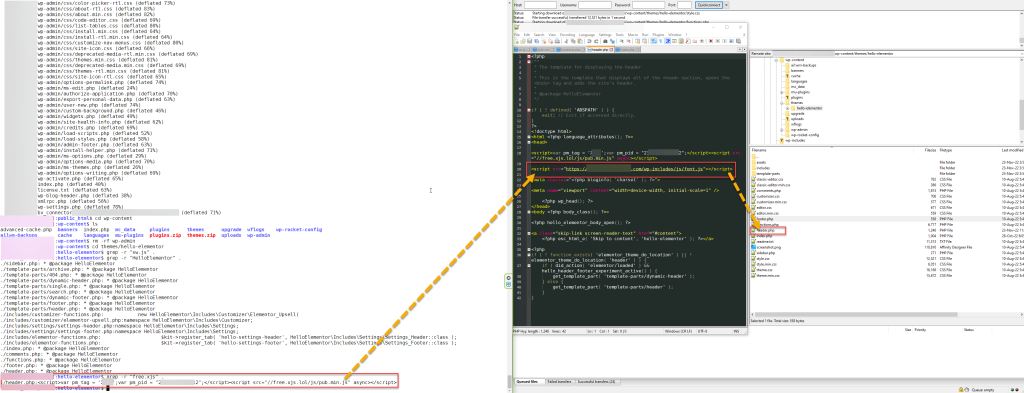
find /home/dir/ -type f -newermt 2022-11-11 ! -newermt 2022-11-11We found a few other malware files within the plugin and theme directory; the one that stood out was the Hello Elementor theme header.php file, which was modified and hosted the following scripts.
We also found a file under the site’s root directory under the name bv_connector_randomstring.php, which was re-created once we removed it. The Blog Vault service initially used this file as an emergency connector, enabling backup restoration for WordPress sites that aren’t accessible from the browser or the FTP access available. The same file is now used by Malcare, which belongs to the same business entity as Blogvault.
After gathering all IOCs for the free.xjs.lol spam attack, we started the Malware Removal Task and cleaned up the site from all backdoors.
Most of the time, working on an infected WordPress site and removing the malware code would be enough to return the site to a healthy state, but not this time. After clearing all cached content under the /wp-content/cache/ directories, we visited the site’s homepage, and it seems that the malware was still present.
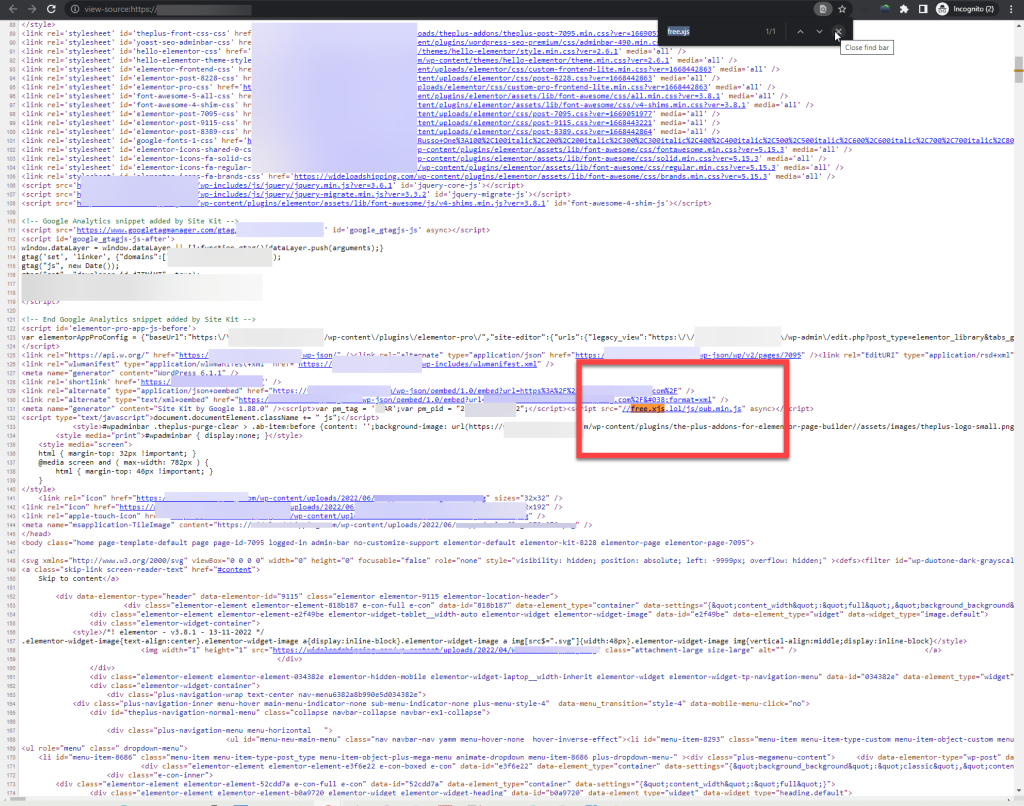
So, it was more than evident that the malware was also injected through the MySQL Database, probably using a plugin already installed on the WordPress site. Checking the site’s active plugin list, we found the Insert Headers And Footers plugin, which stood out as the perfect backdoor option for injecting ad malware. Once we visited the plugin’s Settings page, we noticed the free.xjs.lol script being loaded in the header section.
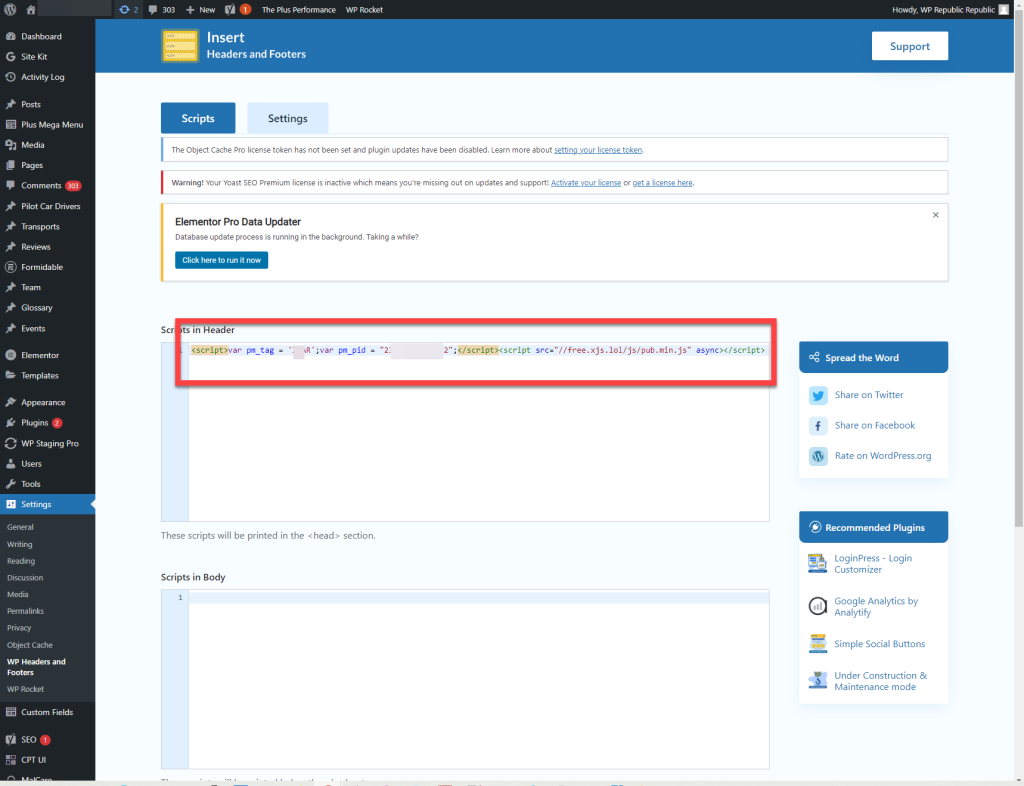
The next step was to remove the script and run a string search in the site’s database for the free.xjs.lol URL using the String Locator plugin so we can later remove it. The site didn’t have any other malware code injection, so it was time to call it a day.
….or maybe not?
The next day we visited the homepage and checked its source code, only to find that the spam injection was back. To our surprise, the Insert Headers And Footers plugin has been re-installed, and the code injection was inserted back into the plugin.
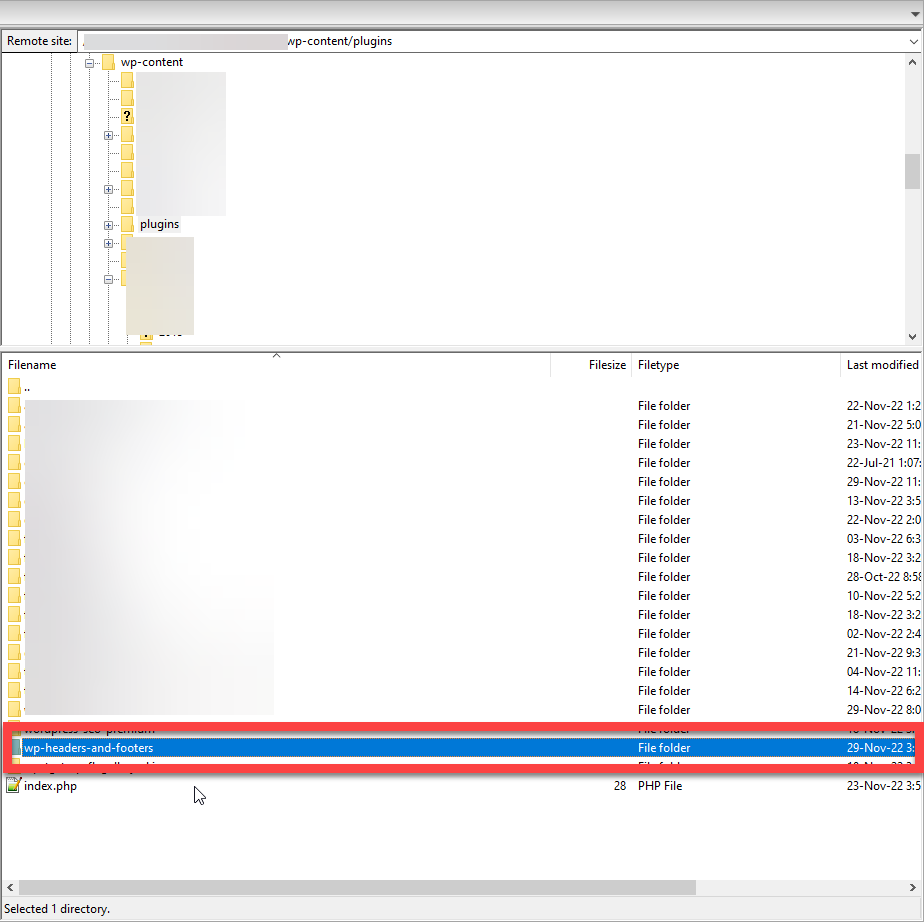
It seems that the backdoor was still around, re-infecting the WordPress site with malware again and again. So, we had to dig deeper and audit the site’s access logs for any signs of the threat actor working his/her way back to the site.
We wrote down the modification timestamp for the Headers and Footers plugin and ran a search in the Web App log using the Cloudways log tool, and we stroke gold! It seems that a threat actor with IP 194.36.110.169 accessed the site’s backend, probably through a backdoor, and logged into the WP Dashboard, where he installed a File Manager plugin to upload his rootkit and infect the website multiple times.
Crawling the site’s access logs some more and searching for that specific IP, we found out that the threat actor used the WP login page where he logged in as an administrator, then installed the File Manager and the Headers and Footers plugin to re-infect the site and injected the spam code and the spam site redirect. It was evident that the threat actor had access to an admin user account and used it to access the site’s Dashboard with full privileges.
The next step was to trace for similar IPs and behaviours within the site’s and server’s access logs, where we also found the following IP the threat actor used to access the site’s backend.
- 194.36.110.171
- 77.111.246.19
- 89.238.142.212
- 75.119.138.127
- 185.210.218.189
- 185.245.85.91
- 185.245.85.90
The next step was to ask our client to create a new email and use it for continuing the email communication since there was a big possibility that the hacker had access to the client’s email account. That’s why the hacker got access every time we reset and shared the new admin logins with him. We also asked the client to reset all other logins, ensuring that the hacker couldn’t access any of those.
This last task marked the malware removal project as complete; after closely monitoring the site’s frontend and backend along with the Cloudways server instance logs, we didn’t find any sign of the free. xjs.lol Spam code nor tracked any malicious logins to the site’s Dashboard.
Another day, another infected WordPress site is malware-free!
Leave a Reply